October 26, 2023 · By Lizzy Herzer
Skip to content 
On this page
basebox Passed the Penetration-Test from Johner Institut With a Very Positive Rating.
We passed a pen test by the renowned Johner Institute with flying colors. We are proud of that and you can read how the test went here.
When we launched the beta version of our data management system basebox, we wanted to make sure that it was secure and reliable for our users. To achieve this goal, we commissioned Johner Institute to perform a Penetration Test, which evaluates the security of system components and applications within a network or software system using means and methods that can penetrate the system without authorization. This type of testing helps to uncover security vulnerabilities that could potentially be exploited by attackers.
Johner Institut is renowned for its expertise in regulatory affairs and can provide assistance to medical device companies in finding the right strategy for regulatory affairs, preparing technical documentation, establishing QM systems, and conducting product testing. Their experience and knowledge in this field made them the perfect partner for us to carry out the pen test.
After conducting the pen test, Johner Institut gave us a "very positive" rating, which confirmed that basebox met their high standards of security and reliability. This was a significant achievement for us, as we know cyber security is the most important within a data management system.
In conclusion, the pen test carried out by Johner Institut was an essential step in ensuring the security and reliability of basebox. We are proud to have passed with flying colors and will continue to work with first class experts like Johner Institut to maintain the highest standards of security for our users.

Conclusion of the Pen Test from Johner Institut
- This assessment provides basebox GmbH with a measure of the current posture in the face of a possible attack or unauthorized use of the services provided by the audited technological infrastructure.
- These results provide the information necessary to develop a progressive and effortful process that will enable the organization to continuously manage the risk posed by the vulnerabilities encountered and to improve its IT security posture for its most valuable assets.
- In the modules analyzed in this exercise, the vulnerabilities are minor and were quickly mitigated, which results in a very robust and secure product.
Authentication is properly implemented, and the fact of being developed 100% in Rust adds an extra secure layer.
Pentesting Reduces Cybersecurity Risks
For us at basebox, cybersecurity is the be-all and end-all.
A company may have solid security protocols in one area, but be deficient in another. Given the high cost of a successful cyber attack, no company should wait until a real-world scenario plays out before going on the offensive. By using penetration testing to uncover gaps in an organization's security layer, security professionals and pen testers can address vulnerabilities before they become a critical liability. As a startup, we believe that the cost of Pen Testing is justified if you value peace of mind and want to prevent future problems.
How a Pen Test Works
The purpose of a pen test is to demonstrate the technical infrastructure of your software.
- During a specified period of time, technical security tests are performed to demonstrate the security level of your software's technological infrastructure that stores, processes, or transmits information, and to determine the possibility of IT attacks by external and/or internal users on the systems that support the organization.
- The primary objective is to ensure the confidentiality, availability and integrity of the information stored in the infrastructure.
- The tests are performed without knowledge of the existing network infrastructure. This method is called "black box" analysis and allows to assess the vulnerability of the system to attacks against the organization by users or companies not associated with the software on the systems defined in the scope.
- The testing of the environment is based on security methodologies that are either internally defined by the tester and/or use internationally recognized and open methodologies such as OSSTMM (Open Source Security Testing Methodology Manual) and OWASP (Open Web Application Security Project).
Systematic approach
- Search for vulnerabilities in the services provided by the organization's external servers.
- Search for vulnerabilities in the organization's web applications.
- Analyzing the results reported by the automatic vulnerability detection systems.
- Manually exploiting the identified vulnerabilities to identify the organization's current risk.
- Identify current risk of the organization.
Methodological approach
The methodology used for the penetration test is as follows:
- Visibility analysis: The assets and all those methods or gateways that can be used to access the organization's resources are identified. The result of this task allows the gene- rating of scorecards with an initial risk assessment based on the exposure of the assets.
- Vulnerability Assessment: Systems are tested for the discovery of existing vulnerabilities. This consists of the following phases:
- Vulnerability research.
- Vulnerability verification.
- Specific Exploitation: Manual evaluation and exploitation of vulnerabilities found. This consists of the following phases:
- Manual vulnerability research.
- Specific Intrusion on vulnerability found
- Identification of countermeasures: Detailed analysis of each of the evidences obtained in the previous phases and proposal of corrective measures, following consensus of the technical team in charge of putting the applications into production.
- Some of the used tools were:
Johner Institute combines several methods
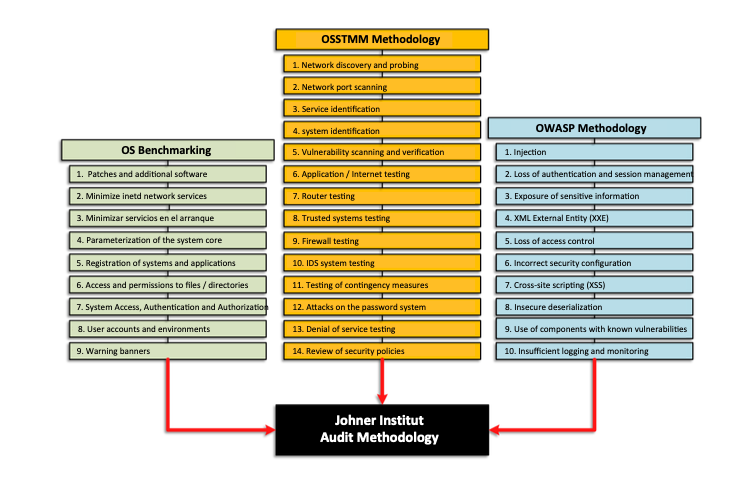
OS Benchmarking
- Patches and additional software
- Minimize initiated network services
- Minimize services at startup
- Parameterization of the system core
- Registration of systems and applications
- Access and permissions to files / directories
- System Access, Authentication and Authorization
- User accounts and environments
- Warning banners
OSSTMM Methodology
- Network discovery and probing
- Network port scanning
- Service identification
- System identification
- Vulnerability scanning and verification
- Application / Internet testing
- Router testing
- Trusted systems testing
- Firewall testing
- IDS system testing
- Testing of contingency measures
- Attacks on the password system
- Denial of service testing
- Review of security policies
OWASP Methodology
- Injection
- Loss of authentication and session management
- Exposure of sensitive information
- XML External Entity (XXE)
- Loss of access control
- Incorrect security configuration
- Cross-site scripting (XSS)
- Insecure deserialization
- Use of components with known vulnerabilities
- Insufficient logging and monitoring
Finally, startups can take note:
When technical due diligence is on the horizon, it also helps to have conducted a pen test or bug bounty program, always assuming that those conducting it are independent, ethical hackers.